What are the Cybersecurity alternatives to VPN?
The remote work revolution is well underway, but are traditional VPNs still the best security blanket? While they served us well in the early days, their limitations become increasingly apparent wi...
What are the Cybersecurity alternatives to VPN?
The remote work revolution is well underway, but are traditional VPNs still the best security blanket? While they served us well in the early days, their limitations become increasingly apparent wi...
The remote work revolution is well underway, but are traditional VPNs still the best security blanket? While they served us well in the early days, their limitations become increasingly apparent with a more distributed workforce. Luckily, a new generation of tools has emerged, offering enhanced security, flexibility, and performance for the remote workspace. Let's dive into the top alternatives to VPNs:
What are the best alternatives to VPN?
- Zero Trust Network Access (ZTNA): ZTNA grants access based on user identity and device trust, not just network location. Imagine each user having a secure tunnel directly to the applications they need, not the entire network, minimising attack surfaces and preventing lateral movement. ZTNA simplifies user experience, scales effortlessly, and keeps your precious data safe from prying eyes.
- Secure Access Service Edge (SASE): Gone are the days of juggling separate network and security tools. SASE converges both functions into a single, cloud-based platform, streamlining management and enhancing visibility. Think of it as a unified control centre for your remote empire, providing secure access, robust threat prevention, and optimised performance, all from one dashboard.
- Software-Defined Wide Area Network (SD-WAN): SD-WAN intelligently routes traffic across the most efficient paths, regardless of underlying infrastructure. Imagine your network adapting to real-time conditions like a nimble traffic cop, ensuring the smoothest, most reliable connection for even the most remote worker.
- Identity and Access Management (IAM): IAM is your gatekeeper, controlling user access to resources based on predefined roles and permissions. Think of it as a smart bouncer verifying IDs and granting access only to authorised personnel. IAM strengthens your security posture by minimising human error and preventing unauthorised access attempts.
- Endpoint Management: Security starts at the source. Endpoint management secures every device accessing your network, from laptops to mobile phones. Imagine each device as a well-fortified sentry, equipped with anti-malware, patching tools, and data encryption, always on guard against cyber threats.
What are the benefits of moving away from VPN?
These alternatives listed above offer multiple, compelling reasons to move beyond VPNs.
- Enhanced Security: Granular access, identity verification, and device-level protection create a layered defence against cyber threats.
- Improved Performance: Efficient routing, cloud-based delivery, and direct application access boost performance for every remote worker.
- Simplified Management: Unified platforms, automated processes, and centralised control reduce IT headaches and streamline operations.
- Greater Scalability: Cloud-based solutions seamlessly adapt to your growing workforce, eliminating the need for complex VPN infrastructure scaling.
[caption id="attachment_12068" align="aligncenter" width="899"]
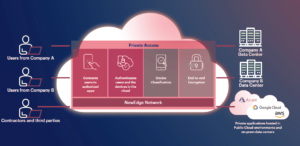
ZTNA is a great alternative to VPN[/caption]
The Time to evolve away from VPNs is now
As the remote work landscape evolves, so should your security and connectivity solutions. Embrace the power of ZTNA, SASE, SD-WAN, IAM, and endpoint management to empower your remote workforce with secure, high-performance access, while taking your organisation's security posture to the next level. Don't get stuck in the VPN tunnel of the past – unlock the potential of the remote revolution with cutting-edge tools built for the future of work.


.svg)
.png)
