IT Security audit - listing the vulnerabilities
“We’re pretty secure here” I’ve heard numerous times. Then that statement is quickly followed by a confession from the prospect telling me about the security access the business has given to off-sh...
IT Security audit - listing the vulnerabilities
“We’re pretty secure here” I’ve heard numerous times. Then that statement is quickly followed by a confession from the prospect telling me about the security access the business has given to off-sh...
“We’re pretty secure here” I’ve heard numerous times. Then that statement is quickly followed by a confession from the prospect telling me about the security access the business has given to off-shore contractor teams. Or that they have no policy for revoking ex-employee log-ins. Or they have old systems that are still deployed and have integration to new secure systems. Like a spare set of badly hidden keys, these vulnerabilities are all easily exploited by different types of hacking. As security measures adapt to new threats, attackers shift their focus to less-secure avenues, seeking to bypass established defences. It's obviously crucial for organisations to maintain awareness of both existing and emerging attack vectors, and continuously update their cybersecurity measures accordingly. So, where can hackers access your data? Where are the vulnerabilities? It’s important to understand that it’s not all about software within a business, but also culture. How is the workforce set-up? What access do 3rd parties have to the data network and how closely are those actors monitored?
What are the Common Vulnerabilities targeted by Hackers?:
Cybercriminals exploit various vulnerabilities, known as attack vectors, to infiltrate organisational systems and steal valuable data or assets. Here are six common vulnerabilities that attackers frequently exploit:
- Network Vulnerabilities:
- Broad East/West Access: This allows unrestricted lateral movement within your network, enabling attackers to easily pivot between systems and exfiltrate sensitive data. Think of it like having open doors between departments, allowing anyone to roam freely.
- Weak Identity and Access Management:
- Excessive Privileges: Granting users more access than needed. Hackers can exploit these privileges to access sensitive data or disrupt operations.
- Missing Sunset Provisions: Failing to regularly revoke unused access allows hackers to easily find and use these log-ins to gain entry.
- Software and Platform Defects:
- Exploitable Flaws in Popular Platforms: Even established platforms like Microsoft Office 365, Salesforce.com, and Google Workspace can have vulnerabilities that hackers target.
- End-of-Life/Obsolete Systems:
- Unpatched Vulnerabilities: These outdated systems allow an entry point into existing systems. Hackers can easily exploit known vulnerabilities in unpatched software and hardware.
- Idiosyncratic Vulnerabilities:
- Unique Infrastructure Exploits: Every organisation has its own quirks, like custom applications or unusual network configurations. Hackers can study these unique features and exploit any “secret entrance” vulnerabilities they find.
- Third-Party Vendor Risks:
- Weaker Defences: Organisations often rely on third-party vendors with access to sensitive data. However, these vendors may have weaker cybersecurity practices, making them easier targets for hackers.
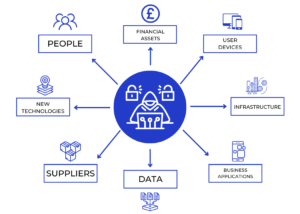
By understanding these common vulnerabilities and taking proactive steps to address them, organisations can significantly reduce their risk of falling victim to cyberattacks. Remember, a strong defence is built layer by layer, plugging every potential entry point and keeping your data safe. When you are listing out all your data and hardware in an audit. Use this list below to easily categorise where the attacks could occur: Business Asset Groups:
- Data
- Financial Assets
- People
- Suppliers
- Infrastructure
- User Controlled devices
- New Technologies
- Applications
Here are the Top 8 attack areas that could be your business’s own security access point for an attacker.

.png)

.svg)
